Solution
Your current position:Home > Solution
Solution
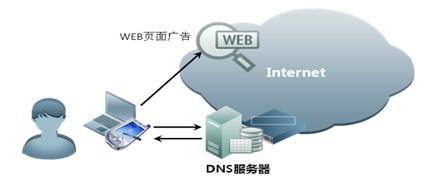
DNS protection solution
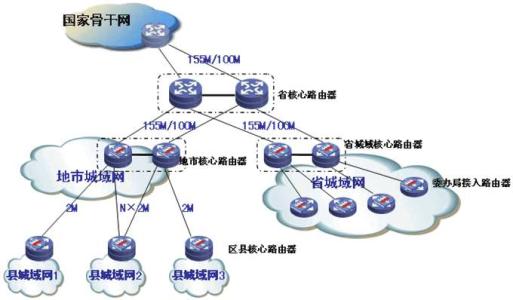
DNS protection solutionWith the continuous development of Internet business, industry competition is becoming more and more fierce, malicious attacks between websites emerge in endlessly, these attacks often use the way of false domain name requests to attack the other side of the domain name server.As the receiver of DNS requests in Metropolitan area Network (man), the operator DNS system is often attacked by this kind of attack, which leads to the failure of the whole network Internet service seriously.
Branch IPSec VPN solution
Branch IPSec VPN solutionThe information of e-government, enterprise, finance, securities and other industries has been deepened, and the demand for the remote connection of the branches is higher.
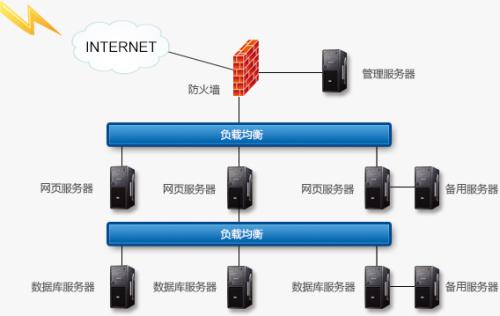
Server load balancing solution
Server load balancing solutionWith the rapid development of the Internet and the continuous enrichment of the business types, how to improve the user experience, make the network access fast and secure, use the server resources more reasonably, and make the operation and maintenance m
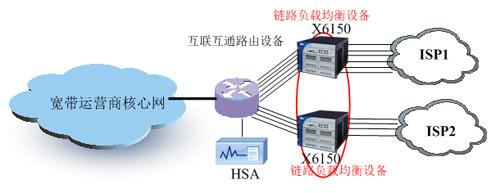
Link load balancing solution
Link load balancing solutionWith the development of information business, the application of data carried by the network is becoming more and more complex, and the requirement of transmission quality is becoming more and more high. How to solve the contradiction between the shortage
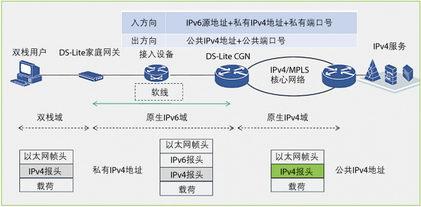
Operator CGN solution
Operator CGN solutionAlthough China has the second largest share of IPv4 addresses in the world, China has the largest number of Internet users in the world, and the number of Internet users is still rising. The IPv4 address resources have long been seriously scarce. At prese
Intelligent WAN solution
Intelligent WAN solutionWith the rapid development of cloud computing technology and Internet of things technology, the continuous development of network business applications, all kinds of new applications continue to emerge. And it is becoming more and more important in the pr
Security protection system scheme
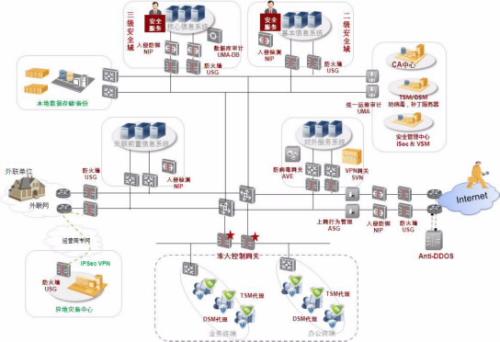
Security protection system schemeThe protection objects and protection levels of a typical data center are from outside to within (i.e., business flow direction, to ensure business security as the goal)


 CHN
CHN